Internal & External Testing
Our testers conduct real-world testing against your products to produce current security vulnerability threat analysis of your systems
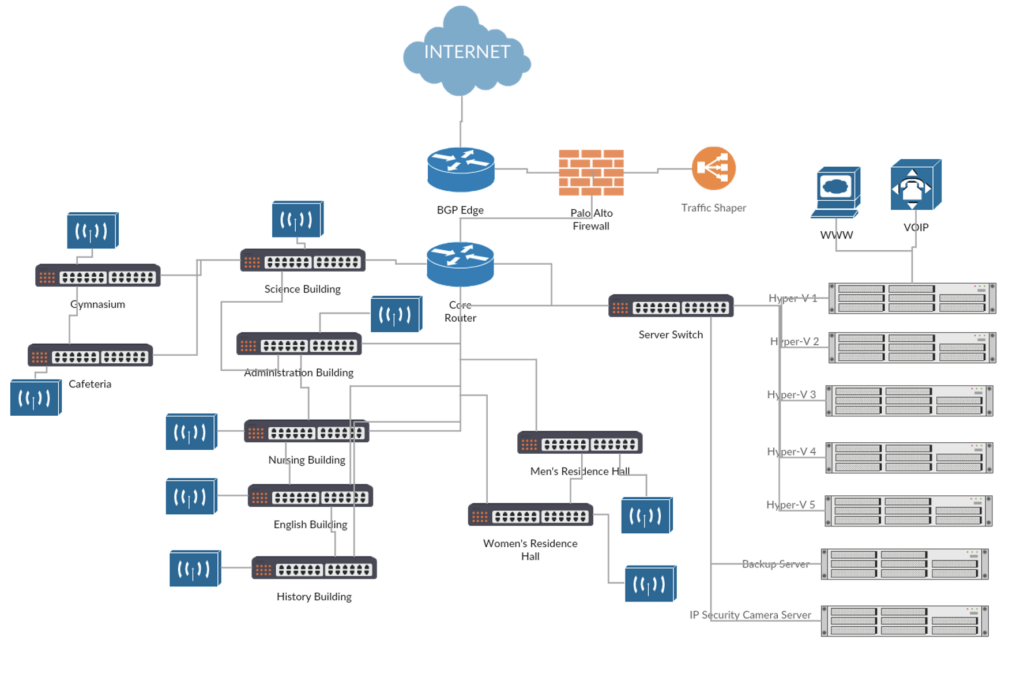
Internet of Things and Network Security
IoT and BYOD are here to stay, our staff are here to help navigate these challenging mazes to help maintain a secure network while still utilizing current technology
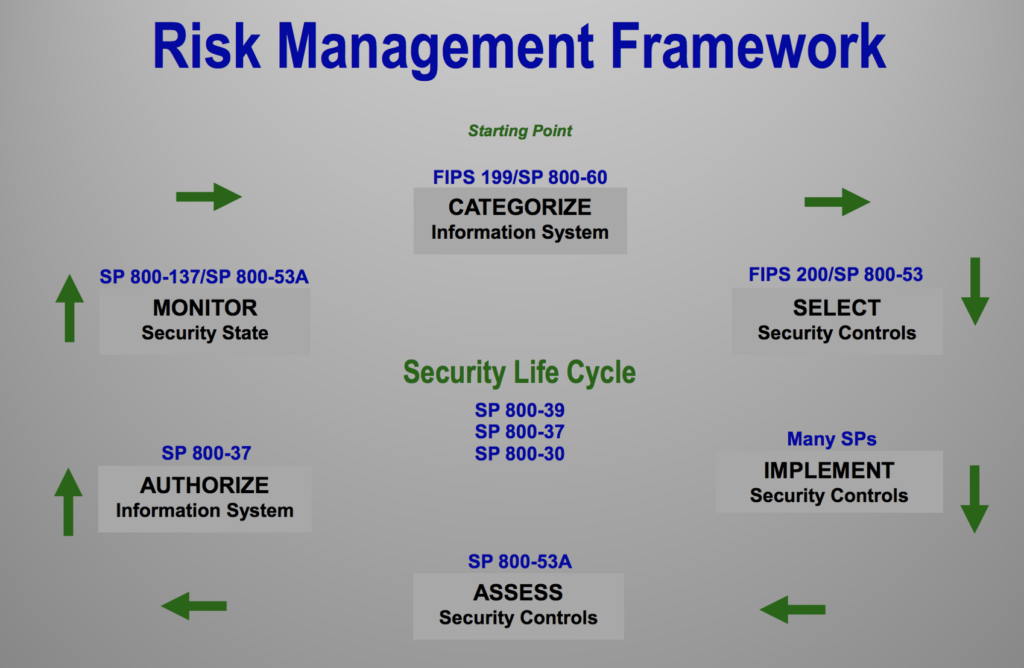
Strategic Engagement
C-Level interaction and inclusion within your security posture is a key element to a successful security program. Our staff can help present and strategize approach that make sense for your company
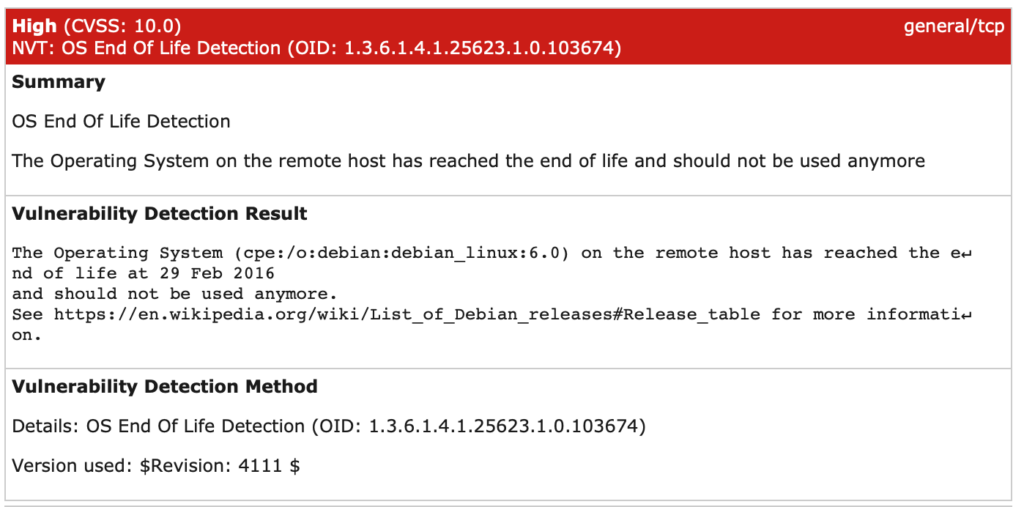
Not just another scanner report
When you hire a pen-tester, you should not accept just a list of results from a scanning tool. Your pen-tester should be able to think like an attacker, and how to utilize that knowledge to get footholds into a system or network.
Our Pen-testers present a comprehensive report of all findings, in both a detailed and summary style that can easily be shown to C-Level personnel. Additionally, we produce mitigation recommendations and strategies to help you navigate the challenges of securing your systems.
Book a consultation today!
